The Digital Technology Blog
Computers • Artificial Intelligence(AI) • IoT • Networking • Cybersecurity • Programming • Architecture • Hardware • Software
JavaScript ES6+ Features Every Developer Should Use
JavaScript ES6+ Features Every Developer Should Use JavaScript has evolved from a simple scripting language into the backbone of modern web, mobile, and cloud applications. ES6, officially known as ECMAScript 2015, marked a turning point by introducing features that dramatically improved readability, maintainability, and performance. Every

LRAD Technology for Military Use
LRAD Technology for Military Use: Digital Sound Weapons and the Future of Non-Lethal Defense LRAD technology has quietly evolved from a crowd-control novelty into a digitally driven, mission-critical military capability. By combining precision acoustics with advanced digital signal processing, modern LRAD systems give armed forces a
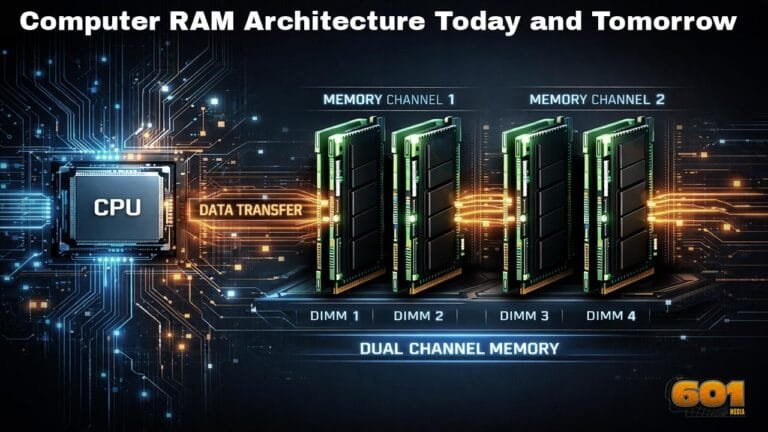
Computer RAM Architecture Today and Tomorrow
Computer RAM Architecture Today and Tomorrow Modern computing performance is shaped as much by memory architecture as by raw processing power. Random Access Memory, commonly referred to as RAM, sits at the center of this performance equation. It bridges the speed gap between ultra-fast processors and

DRAM vs NAND
DRAM vs NAND: Understanding the Two Memory Technologies Powering Modern Computing Modern computing relies on two foundational memory technologies that serve very different but equally critical purposes. DRAM and NAND memory work together to deliver speed, efficiency, and data persistence across devices ranging from smartphones to

Create Video Games & Interactive Media in Unreal Engine 5
Create Video Games & Interactive Media in Unreal Engine 5 Unreal Engine 5 has redefined what is possible in video game development and interactive media creation. Built for high-fidelity visuals, scalable performance, and real-time workflows, it empowers developers to create immersive experiences across games, film, architecture,
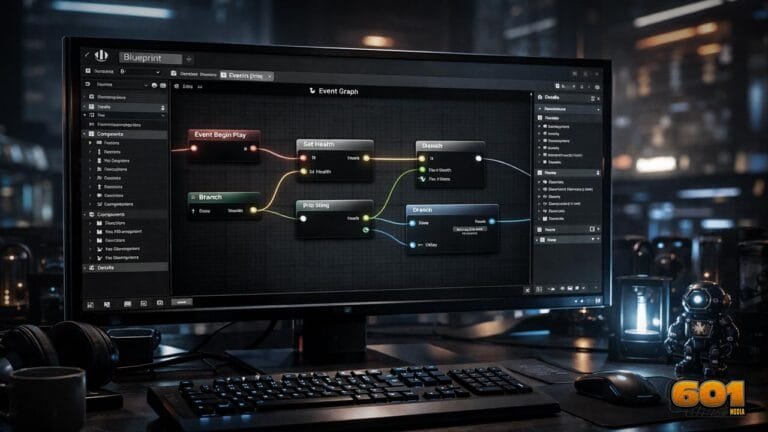
Unreal Engine 5 Blueprints for Beginners
Unreal Engine 5 Blueprints for Beginners Unreal Engine 5 Blueprints provide a visual scripting system that allows beginners to create complex game logic without writing traditional code. By connecting nodes that represent actions, conditions, and events, developers can build gameplay systems faster while maintaining production-level scalability.

How Does a Blockchain Work?
How Does a Blockchain Work? Blockchain technology has evolved from a niche cryptographic experiment into a foundational digital infrastructure reshaping finance, supply chains, healthcare, and governance. At its core, a blockchain is a distributed, tamper-resistant ledger that records transactions across a decentralized network of computers. Todays
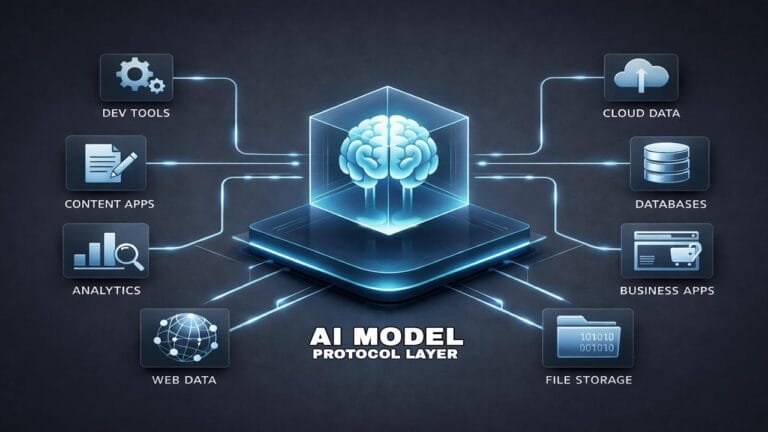
What Does MCP (Model Context Protocol) Do?
What Does MCP (Model Context Protocol) Do? The Model Context Protocol (MCP) is an emerging open standard that allows large language models (LLMs) to securely and consistently access external tools, data sources, and services. It solves a core limitation of modern AI systems: the inability to

Digital Technology Past and Future
Digital Technology: Past Foundations and Future Frontiers A clear-eyed exploration of how digital technology emerged, how it reshaped industries, and where it is headed next, with strategic insights for leaders navigating accelerating technological change. Table of Contents The Origins of Digital Technology The Internet and Platform

GPU vs TPU vs LPU: A Technical Guide to AI Hardware
GPU vs TPU vs LPU: A Technical Guide to AI Hardware AI hardware can feel intimidating at first, like walking into a city where every street sign is written in acronyms. GPUs, TPUs, LPUs, FLOPS, tensors, latency, throughput. It is a lot. Take a breath. You
What is Self-Reflection in AI?
What is Self-Reflection in AI? Artificial Intelligence (AI) technology is advancing rapidly, and one of the emerging frontiers is self-reflection in AI—a concept that aims to enable AI systems to assess, understand, and optimize their behavior. While self-reflective AI is still primarily aspirational, it introduces new

Blockchain Real World Uses
Blockchain. It sounds futuristic, doesn’t it? Like something out of a sci-fi movie. But it’s so much more than just a buzzword. It’s a technology that’s already changing the way we think about transactions, trust, and transparency. Think of it as a public ledger on steroids,

IoT Security
IoT Security, imagine a world where your refrigerator can order milk for you when you run out, your thermostat learns your daily routine and sets the temperature to your liking, and your car starts itself on a cold winter morning. This isn’t a sci-fi movie—welcome to

What are MySQL Stored Procedures?
Stored procedures in MySQL are a powerful feature that allows developers to encapsulate a series of SQL statements into a single, reusable object. This article delves deep into the world of MySQL stored procedures, shedding light on their benefits, how they work, and how they can

What is NMap?
NMap, short for “Network Mapper,” is a powerful and versatile open-source tool used by network administrators, security professionals, and hackers alike. Its primary purpose is to discover devices running on a network and find open ports along with various attributes of the network. As the digital

Basics of NMAP
NMAP, which stands for Network Mapper, is a powerful and versatile open-source tool used by network administrators, security professionals, and hackers alike. Its primary function is to discover devices running on a network and find open ports along with various attributes of the network. Given the

Hacking TCP/IP
The Transmission Control Protocol/Internet Protocol (TCP/IP) is the backbone of the internet and most local networks. It’s the suite of communications protocols used to connect hosts on the internet. But like any technology, it’s not immune to vulnerabilities. This article aims to shed light on the

MySQL for Beginners
MySQL, a name that resonates with many in the tech industry, is a cornerstone of modern database management. But what exactly is it, and why is it so popular? This article aims to demystify MySQL for beginners, offering a comprehensive overview of its functionalities, benefits, and




