The Digital Technology Blog
Computers • Artificial Intelligence(AI) • IoT • Networking • Cybersecurity • Programming • Architecture • Hardware • Software

How VPNs Work
How VPNs Work: Security, Encryption, and Use Cases A VPN (Virtual Private Network) creates an encrypted “tunnel” between your device and a VPN server, reducing eavesdropping risk on untrusted networks, masking your IP address from the sites you visit, and enabling secure access to private resources.
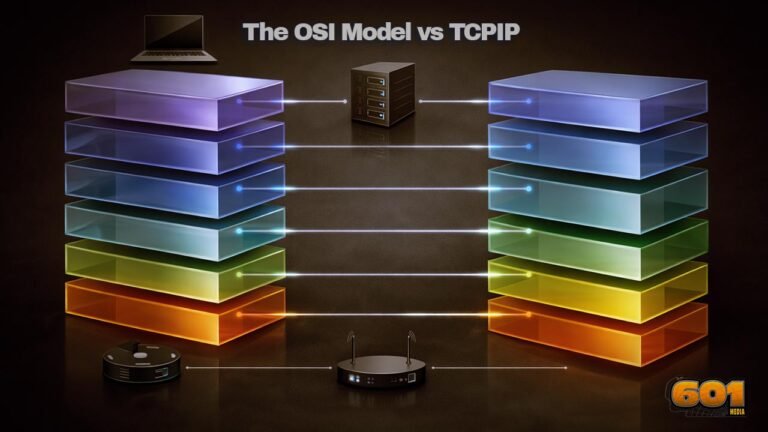
The OSI Model vs TCP/IP
The OSI Model vs TCP/IP: What Every Techie Should Know Two networking models dominate how we explain, design, secure, and troubleshoot modern systems: the OSI reference model and the TCP/IP (Internet protocol suite) model. The OSI model is a conceptual framework created to standardize how networked

The Cloudflare Stack Explained
The Cloudflare Stack Explained: Edge Security, Performance, and Compute Cloudflare has evolved from a content delivery network into one of the most comprehensive edge-based platforms in the world. Its stack blends networking, security, compute, and developer tooling into a single, globally distributed system designed to make

In-House Data Recovery
In-House Data Recovery: A Strategic Advantage for Modern Enterprises In-house data recovery refers to an organization’s ability to diagnose, repair, and restore lost or corrupted data using internal resources rather than relying on external service providers. As data volumes expand and operational dependence on digital systems

Sub-1nm Chip Fabrication Methods Explained
Sub-1nm Chip Fabrication Methods Explained Sub-1nm chip fabrication represents the most extreme frontier of semiconductor manufacturing, where innovation shifts from traditional scaling to atomic-level engineering, novel materials, and three-dimensional architectures to sustain performance gains beyond Moore’s Law. Table of Contents Why Sub-1nm Is a Fundamental Challenge
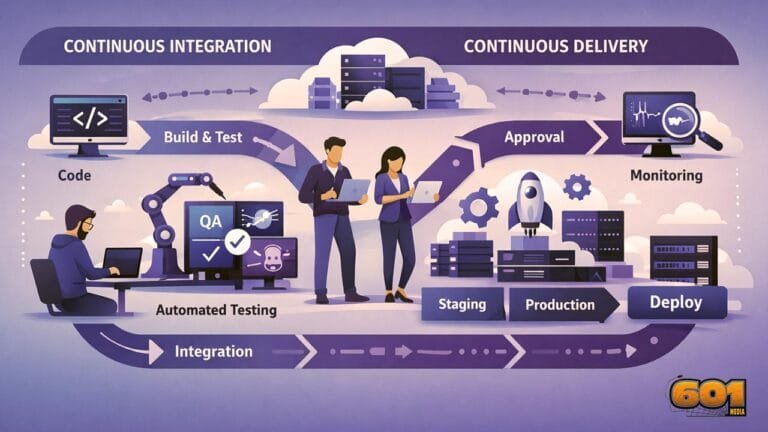
Intro to DevOps: CI/CD Essentials
Intro to DevOps: CI/CD Essentials for High-Performing Tech Teams Modern software delivery is no longer defined by speed alone. It is defined by reliability, repeatability, and the ability to adapt without breaking production systems. DevOps emerged as a response to these demands, and at the center

Building REST APIs with Python Using Flask and Django
Building REST APIs with Python Using Flask and Django Modern digital products depend on fast, secure, and scalable communication between systems. REST APIs power that communication layer, enabling web apps, mobile apps, IoT devices, and enterprise platforms to exchange data reliably. Python has emerged as a
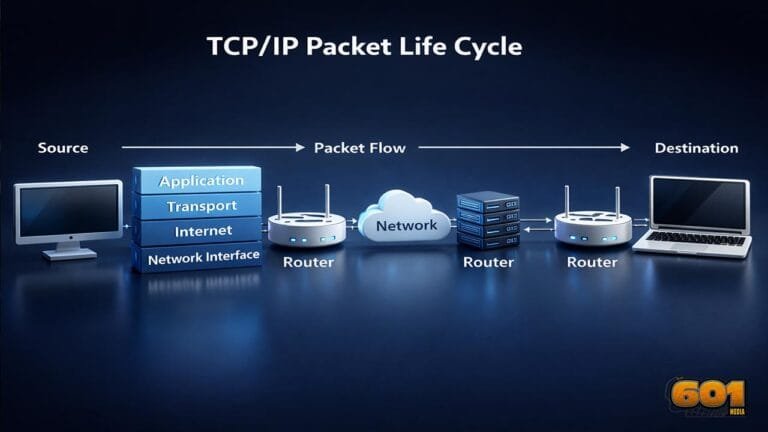
Explaining the TCP/IP Packet Life Cycle
Explaining the TCP/IP Packet Life Cycle A TCP/IP packet does not simply move from one computer to another. It is created, wrapped, addressed, transmitted, routed, verified, acknowledged, and finally reassembled. Understanding this life cycle is essential for anyone working in networking, cloud infrastructure, cybersecurity, or modern
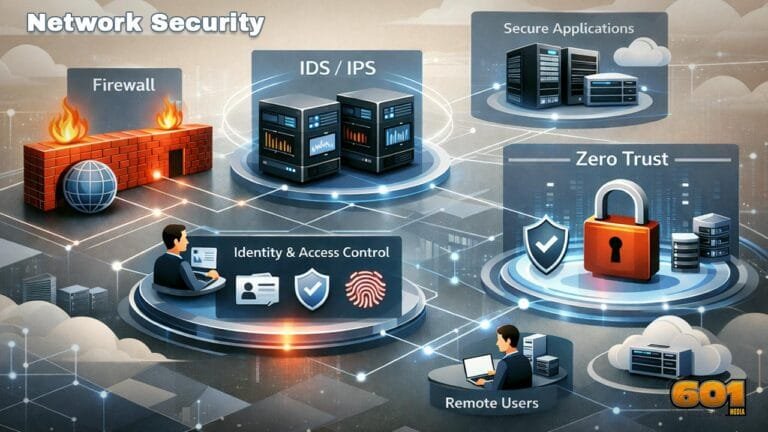
Network Security: Firewalls, IDS/IPS, and Zero Trust Explained
Network Security: Firewalls, IDS/IPS, and Zero Trust Explained Network security has shifted from “keep attackers out” to “limit trust everywhere.” Firewalls reduce exposure, IDS/IPS detects and blocks hostile behavior, and Zero Trust changes how access is granted so a single compromise does not become a full-network

Intro to Ethical Hacking
Intro to Ethical Hacking: Tools, Techniques & Ethics Ethical hacking is the disciplined practice of identifying, testing, and fixing security vulnerabilities before malicious attackers can exploit them. We explain what ethical hacking is, why it matters, the tools and techniques professionals use, and the ethical boundaries

IPv4 vs IPv6: Why the Internet Is Moving On
IPv4 vs IPv6: Why the Internet Is Moving On The internet is undergoing one of its most important infrastructure transitions since its creation. While most users never see it, the shift from IPv4 to IPv6 is reshaping how devices connect, scale, and remain secure in a

Next-Generation Lithography Technology and the Future of Semiconductors
Next-Generation Lithography Technology and the Future of Semiconductors The semiconductor industry is approaching physical limits that once seemed theoretical. As transistors shrink below five nanometers, traditional lithography methods struggle to maintain precision, yield, and cost efficiency. Next-generation lithography technology is the defining factor that will determine
X-ray Lithography in Semiconductor Manufacturing Explained
X-ray Lithography in Semiconductor Manufacturing Explained X-ray lithography has long been viewed as one of the most technically ambitious approaches to semiconductor patterning. As transistor dimensions push beyond the limits of extreme ultraviolet lithography, X-ray lithography is re-emerging as a potential pathway to sustain Moore’s Law

X-ray Lithography vs EUV Lithography
X-ray Lithography vs EUV Lithography: Key Differences and Industry Impact Manufacturing Modern semiconductor manufacturing is defined by how precisely engineers can pattern features measured in nanometers. As transistor sizes shrink and chip complexity explodes, lithography has become the primary bottleneck—and the primary differentiator—in advanced fabrication. Two
How X-ray Lithography Could Transform Chip Manufacturing
How X-ray Lithography Could Transform Chip Manufacturing. X-ray lithography has long been discussed as a breakthrough alternative to extreme ultraviolet lithography. As semiconductor scaling approaches physical and economic limits, this technology is re-emerging as a potential way to redefine how advanced chips are designed, patterned, and

AI Chip Sales Performance
AI Chip Sales Performance: A Data-Driven Overview of Market Growth, Leaders, and Future Trajectory AI chip sales have emerged as one of the strongest indicators of technological momentum in the global digital economy. As artificial intelligence moves from experimentation to large-scale deployment, demand for specialized computing

What Is Website Hardening?
What Is Website Hardening? A Practical Guide to Securing Modern Websites Website hardening is the systematic process of reducing a website’s attack surface by eliminating vulnerabilities, tightening configurations, and enforcing strict security controls across the application, server, and network layers. The goal is simple: make the

Top Emerging Cyber Threats of 2026
Top Emerging Cyber Threats of 2026 and How to Defend Against Them Cyber risk in 2026 is being reshaped by two forces moving at the same time: attackers are industrializing social engineering with AI, and defenders are racing to reduce whole classes of technical weakness (identity




