Explaining the TCP/IP Packet Life Cycle
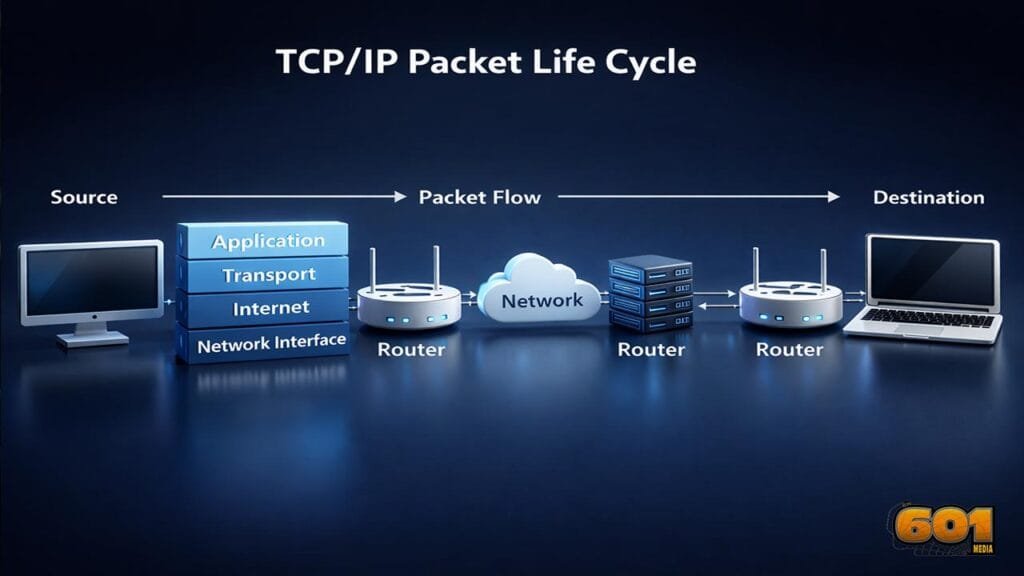
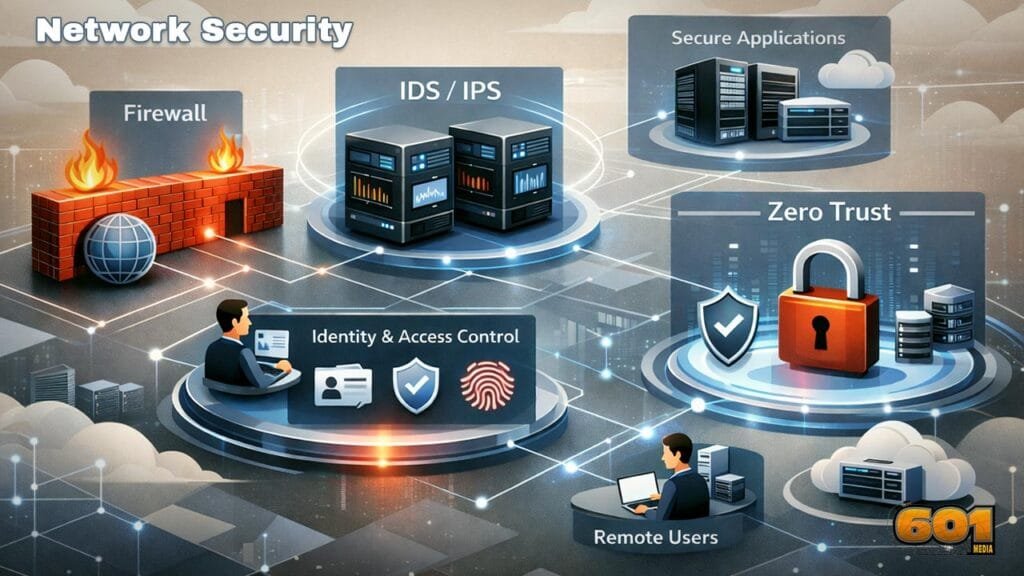
Explaining the TCP/IP Packet Life Cycle A TCP/IP packet does not simply move from one computer to another. It is created, wrapped, addressed, transmitted, routed, verified, acknowledged, and finally reassembled. Understanding this life cycle is essential for anyone working in networking, cloud infrastructure, cybersecurity, or modern software systems. Table of Contents Understanding the TCP/IP Model […]
Explaining the TCP/IP Packet Life Cycle Read More »