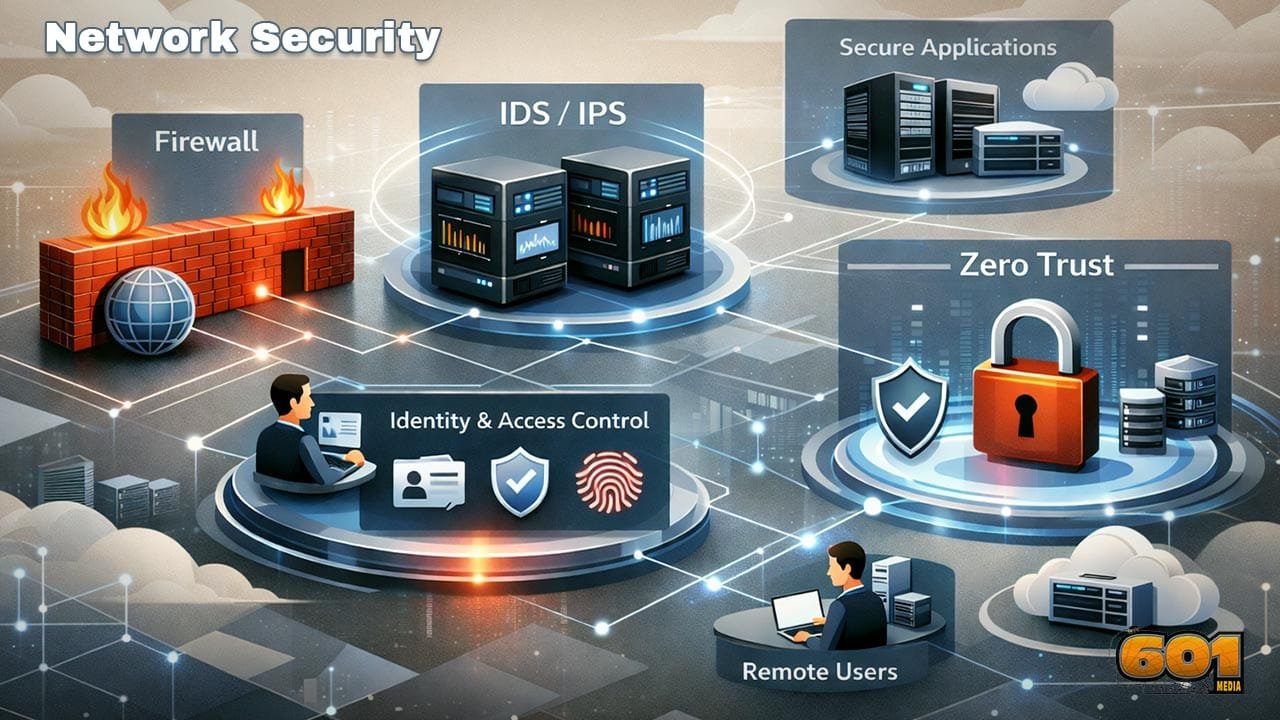
Network Security: Firewalls, IDS/IPS, and Zero Trust Explained
Network security has shifted from “keep attackers out” to “limit trust everywhere.” Firewalls reduce exposure, IDS/IPS detects and blocks hostile behavior, and Zero Trust changes how access is granted so a single compromise does not become a full-network incident. Our guide explains what each does, where it fits, and how to combine them into a practical, modern security architecture.
Table of Contents
- Understanding Modern Network Security
- Firewalls: The Control Plane for Traffic
- IDS/IPS: Detecting and Stopping Malicious Activity
- Zero Trust: A Security Model, Not a Product
- How Firewalls, IDS/IPS, and Zero Trust Work Together
- Implementation Playbook
- Top 5 Frequently Asked Questions
- Final Thoughts
- Resources
Understanding Modern Network Security
Network security is the discipline of protecting data, systems, and services as traffic moves between users, applications, and infrastructure. The traditional approach assumed a clear perimeter: the corporate network was “inside,” and everything else was “outside.” That model breaks down when your users work remotely, your workloads run in multiple clouds, and your applications rely on APIs and third-party services. Today, most incidents are not one-step break-ins. They are multi-stage campaigns: initial access, privilege escalation, lateral movement, persistence, and data theft or extortion. A modern security program must reduce exposure, detect abnormal behavior quickly, and constrain what any identity (human or machine) can access if compromised.
Why the Threat Landscape Changed
Two trends explain why “perimeter-only” security fails. First, more work happens off-network: cloud consoles, SaaS apps, and remote endpoints. Second, attackers regularly abuse legitimate credentials and user actions rather than brute-force their way through obvious “blocked” doors. Verizon’s 2024 DBIR highlights that a non-malicious human element is involved in a large share of breaches, reinforcing that security has to be designed for human error and social engineering, not just malware signatures. Breach impact is also financially significant. IBM’s Cost of a Data Breach Report 2024 reports a global average breach cost in the multi-million-dollar range, with meaningful year-over-year movement and variations by sector and region. These numbers matter because they justify investments in controls that reduce blast radius and shorten detection-to-containment time.
Defense-in-Depth vs. Zero Trust
Defense-in-depth means you use multiple layers of controls so no single failure becomes catastrophic. Firewalls, IDS/IPS, endpoint protection, identity controls, logging, and response processes all contribute. Zero Trust fits inside this concept but changes the default assumption: do not trust a connection just because it came from an internal IP range. In practice, a strong architecture blends both. Firewalls still matter for segmentation and exposure reduction. IDS/IPS still matters for detecting exploitation, scanning, and command-and-control behavior. Zero Trust provides the access model that ties identity, device posture, and policy enforcement together.
Firewalls: The Control Plane for Traffic
A firewall is a traffic enforcement point. It evaluates flows (connections) and decides whether to allow, block, or inspect them based on rules. Firewalls are essential because they reduce your attack surface: services you never expose are services attackers cannot easily reach. Modern environments typically use multiple firewall “forms” at once: internet edge firewalls, internal segmentation firewalls, cloud security groups and network ACLs, and web application firewalls (WAFs) in front of HTTP-based apps. The goal is not a single giant rulebase. The goal is targeted control points aligned to how your applications actually communicate.
Types of Firewalls and What They Inspect
- Packet-filtering (L3/L4): Filters by IP, port, protocol, and basic state. Fast and foundational, but limited context.
- Stateful inspection: Tracks connection state, making it harder for spoofed or abnormal packets to slip through.
- Next-generation firewall (NGFW): Adds application awareness, user identity mapping, and often built-in IPS features.
- Web application firewall (WAF): Protects HTTP/S applications from common web attacks (for example, injection patterns) and bot abuse.
- Cloud-native controls: Security groups, network ACLs, and managed firewall services that enforce policy close to workloads.
Firewall Rule Hygiene and Segmentation
Firewall value depends on rule quality. In real organizations, rulebases “rot” over time: emergency openings remain permanent, owners change, and nobody removes legacy access. The result is a permissive environment that looks protected but behaves like a flat network.
- Default-deny for inbound exposure: Publish only what you must (and preferably behind a reverse proxy/WAF).
- Least privilege east-west: Limit internal traffic between subnets, apps, and tiers to only required ports and destinations.
- Segment by risk: Separate identity systems, admin interfaces, production data stores, and third-party connections.
- Rule ownership and review: Every rule should have an owner, purpose, and expiration or review cycle.
- Log what matters: Log denies and sensitive allows. Feed logs into centralized monitoring for correlation.
Where Firewalls Struggle
Firewalls cannot “prove” that a user is legitimate; they can only enforce traffic policy. If an attacker uses valid credentials or tunnels over permitted protocols (especially encrypted ones), a firewall may see “allowed traffic.” Firewalls also struggle to interpret intent in modern application flows, where microservices, APIs, and dynamic ports complicate static rules. This is why firewalls are necessary but not sufficient. You need controls that inspect behavior and detect exploitation patterns, and you need an access model that continuously validates identity and device trust.
IDS/IPS: Detecting and Stopping Malicious Activity
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) monitor network traffic for malicious patterns and suspicious behavior. The difference is action: IDS alerts, IPS blocks (or resets) traffic. In many environments, IPS features are embedded within NGFW platforms, while IDS is used for broader visibility and forensic context. IDS/IPS is especially valuable where attackers attempt to exploit vulnerabilities, scan for weaknesses, or move laterally after an initial foothold. It can spot patterns a firewall rule cannot capture, such as known exploit signatures, protocol anomalies, and command-and-control beacons.
IDS vs. IPS (And When You Need Each)
- IDS: Use when you want maximum visibility with minimal risk of interrupting business traffic. Ideal for monitoring internal segments, DMZs, and cloud traffic mirrors.
- IPS: Use when you need inline protection at choke points (internet edge, critical segmentation boundaries, high-risk service ingress).
- Both: Many mature programs run IPS inline for high-confidence detections and IDS out-of-band for broader hunting and validation.
Signature, Behavioral, and Hybrid Detection
Most IDS/IPS engines blend approaches. Signature-based detection matches known malicious patterns. It is accurate for known threats but weak against novel attacks. Behavioral or anomaly-based detection looks for deviations from baseline behavior, which can uncover new attacks but tends to require tuning to reduce false positives.
- Signature-based strengths: High precision for known CVE exploitation patterns and commodity malware.
- Behavioral strengths: Better at identifying unusual lateral movement, rare protocol usage, or abnormal data exfiltration behavior.
- Hybrid approach: Use signatures for blocking and behavioral analytics for investigation and continuous improvement.
Tuning, Alert Quality, and SOC Workflow
The biggest operational risk in IDS/IPS programs is alert overload. If everything is urgent, nothing is urgent. High-performing security teams treat detection engineering like product management: they prioritize detections tied to real business risk, measure false-positive rate, and iterate.
- Start in detect mode: Baseline traffic, then selectively enable prevention for high-confidence rules.
- Use asset context: A scan against a public web server is different from a scan against an identity store.
- Integrate with response: Alerts should create tickets, enrich with context, and map to playbooks.
- Review post-incident: Every incident should produce improved rules, better segmentation, or tighter Zero Trust policy.
Zero Trust: A Security Model, Not a Product
Zero Trust is a model that assumes breach and removes implicit trust. Instead of granting broad access because a user “is on the VPN” or “is inside the network,” Zero Trust continuously verifies identity, device posture, and context, and it limits access to the minimum necessary for the task. This matters because modern attacks often use legitimate channels: stolen credentials, session hijacking, OAuth abuse, and compromised endpoints. Zero Trust reduces the probability that a single compromised identity turns into organization-wide lateral movement.
NIST View of Zero Trust Architecture
NIST SP 800-207 describes Zero Trust as an approach that shifts defenses from static, network-based perimeters to focus on users, assets, and resources. It outlines logical components, policy decision points, and the need for strong identity, telemetry, and policy enforcement. This framing helps organizations avoid “Zero Trust as a logo” and instead treat it as an architectural change.
Core Pillars and Cross-Cutting Capabilities
A practical way to operationalize Zero Trust is through maturity models. CISA’s Zero Trust Maturity Model frames Zero Trust across pillars (such as identity, device, network/environment, application/workload, and data) plus cross-cutting capabilities like visibility/analytics and automation/orchestration.
- Identity: Strong authentication, conditional access, and least privilege.
- Device: Device inventory, posture checks, and endpoint risk signals.
- Network/environment: Segmentation, controlled pathways, and policy enforcement points.
- Application/workload: Strong service identity, secure APIs, and runtime protections.
- Data: Classification, encryption, and access governance.
- Visibility and analytics: Telemetry to detect abnormal behavior and drive adaptive access.
- Automation and orchestration: Faster containment and consistent enforcement at scale.
ZTNA, Microsegmentation, and Identity
Zero Trust Network Access (ZTNA) replaces the “all-or-nothing” VPN model with application-specific access. Users authenticate, devices are evaluated, and access is granted to only the required application, not the entire network. Microsegmentation applies the same concept inside environments: workloads can only talk to the exact dependencies they need. This is where Zero Trust intersects with firewalls and IDS/IPS. Firewalls and segmentation gateways become enforcement points. IDS/IPS and telemetry become the feedback loop that informs risk and policy updates.
How Firewalls, IDS/IPS, and Zero Trust Work Together
These controls solve different problems and should be designed as a system. Firewalls are the policy gate for traffic pathways. IDS/IPS detects and blocks hostile behavior on those pathways. Zero Trust defines who and what is allowed to use those pathways, under what conditions, and with what continuous verification.
A Practical Reference Architecture
- Edge protection: Internet-facing services sit behind a WAF/reverse proxy and an NGFW. Only required ports are exposed.
- Segmentation boundaries: Internal segmentation firewalls separate user networks, server tiers, and sensitive services.
- Inline IPS at choke points: Block high-confidence exploits, scanning, and known command-and-control patterns.
- Out-of-band IDS visibility: Mirror key segments for threat hunting and forensic investigation.
- ZTNA for remote access: Replace broad VPN access with app-scoped access tied to identity and device posture.
- Central logging and correlation: Firewall, IDS/IPS, endpoint, and identity logs feed a SIEM/SOAR workflow.
When these elements are integrated, you get a compounding benefit: segmentation reduces noise, IDS/IPS becomes more accurate, and Zero Trust policies are easier to enforce because access paths are intentionally designed rather than accidental.
Common Use Cases
- Ransomware containment: Segmentation firewalls limit east-west spread; IDS/IPS flags lateral movement; Zero Trust reduces privilege and blocks risky sessions.
- Cloud workload protection: Cloud security groups enforce least-privilege traffic; IDS sensors monitor mirrored traffic; service-to-service identity enforces Zero Trust between workloads.
- Third-party access: Vendors receive ZTNA access to a single app; firewall rules restrict network reach; IPS watches for scanning or unexpected protocols.
- Executive access protection: Conditional access and device posture checks enforce Zero Trust; firewall segmentation isolates sensitive data; IDS/IPS monitors for unusual data transfer patterns.
Implementation Playbook
A successful rollout is staged. Trying to “do Zero Trust” across the entire organization at once usually fails because it mixes architecture, identity, operations, and culture. Instead, treat it as an innovation program: start with measurable outcomes, run pilots, instrument telemetry, then scale.
Quick Wins in 30–90 Days
- Inventory and map flows: Identify critical apps, their dependencies, and the minimum required network paths.
- Firewall cleanup sprint: Remove unused inbound rules, document owners, and implement rule review cadence.
- Enable segmentation for crown jewels: Put identity stores, admin interfaces, and critical databases behind stricter controls.
- Deploy IDS in visibility mode: Start collecting data, tune alerts, and build top detections tied to your environment.
- Strengthen identity: Enforce MFA, reduce standing privileges, and adopt conditional access for high-risk apps.
Measuring Maturity and Progress
Security programs improve when they measure the right things. A Zero Trust initiative is not “done” when a product is purchased; it is done when risk decreases in measurable ways. Useful metrics include reduction in exposed services, reduction in lateral movement paths, improved time-to-detect, improved time-to-contain, and improved access policy coverage for critical applications. Maturity models (like CISA’s) help translate strategy into a roadmap: initial capabilities (visibility and basic controls), advanced capabilities (policy-driven segmentation and stronger identity signals), and optimal capabilities (adaptive access driven by analytics and automation).
Pitfalls to Avoid
- Over-permissive “temporary” rules: Temporary firewall rules often become permanent. Time-box and audit them.
- IPS everywhere, immediately: Inline blocking without tuning can disrupt the business. Start with high-confidence rules.
- Zero Trust as rebranding: If access is still broad after login, the model has not changed.
- Ignoring machine identities: APIs and service accounts are frequently targeted; apply least privilege and monitoring.
- No operational ownership: Controls need ongoing tuning, reviews, and response workflows, not just deployment.
Top 5 Frequently Asked Questions
Final Thoughts
The most important takeaway is this: modern network security is about controlling trust, not just filtering packets. Firewalls reduce exposure and create deliberate pathways. IDS/IPS watches those pathways and stops known bad behavior while providing visibility into abnormal patterns. Zero Trust changes the access model so identities and devices must continuously prove they are safe, and so access is scoped to what is needed, when it is needed. If you want a practical starting point, prioritize three outcomes: minimize inbound exposure, segment the systems that matter most, and enforce identity-driven access for critical applications. Then add telemetry and tuning so your controls improve over time. This is how security teams build resilience against real-world attack chains, where the first compromise is rarely the last step.
Resouses
- IBM Cost of a Data Breach Report 2025 (overview page)
- IBM Cost of a Data Breach Report 2024 (PDF)
- NIST SP 800-207: Zero Trust Architecture (PDF)
- NIST CSRC: SP 800-207 landing page
- CISA Zero Trust Maturity Model v2.0 (PDF)
- Verizon 2024 Data Breach Investigations Report (PDF)
- Verizon DBIR 2024 highlights page
I am a huge enthusiast for Computers, AI, SEO-SEM, VFX, and Digital Audio-Graphics-Video. I’m a digital entrepreneur since 1992. Articles include AI assisted research. Always Keep Learning! Notice: All content is published for educational and entertainment purposes only. NOT LIFE, HEALTH, SURVIVAL, FINANCIAL, BUSINESS, LEGAL OR ANY OTHER ADVICE. Learn more about Mark Mayo